AWS: Custom Config Rule
-- Explain Custom config with an example?
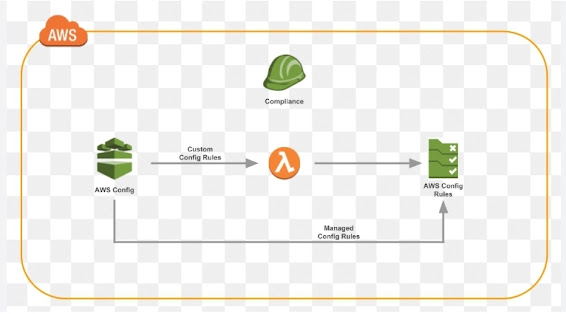
-- Custom config rules in AWS Config allow you to define your own rules to evaluate the configuration settings of your AWS resources. These rules help ensure that your resources are compliant with your organization's requirements and best practices. A custom config rule is created using AWS Lambda functions that evaluate the resource configurations and return a compliance status.
{
"ConfigRuleName": "Sumodh c Sabu",
"Description": "Checks if S3 buckets have server-side encryption enabled.",
"InputParameters": {},
"Scope": {
"ComplianceResourceTypes": [
"AWS::S3::Bucket"
]
},
"Source": {
"Owner": "CUSTOM_LAMBDA",
"SourceIdentifier": <<arn name>>
}
}
-- In this example, the custom config rule is named "Sumodh c Sabu" and its purpose is to verify if S3 buckets have server-side encryption enabled. The `InputParameters` field can be used to pass additional information to the Lambda function, but it's empty in this case.
--Parameters used are as follows:-
a) The `Scope` field specifies that the rule applies to resources of type "AWS::S3::Bucket" only. You can modify this field to apply the rule to other resource types as needed.
b) The `Source` field specifies the source of the custom rule, which is a Lambda function in this case. The `Owner` field is set to "CUSTOM_LAMBDA" to indicate that the rule is a custom rule using a Lambda function.
c) The `SourceIdentifier` field contains the ARN of the Lambda function that performs the evaluation.
-- Once you create and enable this custom config rule, it will be periodically executed by AWS Config to check the compliance status of the specified S3 buckets. If any bucket is found to be non-compliant, AWS Config will provide the necessary information to help you remediate the issue.
-- Custom config rules provide a flexible way to enforce compliance policies and ensure that your AWS resources are properly configured according to your organization's standards.
Thank you




Comments
Post a Comment